Microsoft Expands Token Protection to Entra ID P1: What You Need to Know

Microsoft has just made a significant security enhancement available to a broader audience: Token Protection for Conditional Access is now supported under Microsoft Entra ID P1 licenses. This update gives more organisations access to powerful tools that help prevent token theft and session hijacking, without needing to upgrade to Entra ID P2.
Here’s what this means, why it matters, and how you can start using it.
What Is Token Protection?
Token Protection is a security feature in Microsoft Entra Conditional Access that ensures refresh tokens are bound to the device they’re issued on. If that token is stolen or copied, it simply won’t work on another device – effectively neutralising many common attack vectors like session replay or man-in-the-middle token theft.
Until recently, this feature was limited to organisations with the Entra ID P2 licensing. That’s now changed.
✅ Now Available to P1 License Holders
Microsoft has quietly updated its official documentation, confirming that Token Protection is now included with Entra ID P1. That means if you’re using Microsoft 365 Business Premium, E3, or hold standalone P1 licenses, you now have access to this enterprise-grade feature - without any additional cost or licensing tier upgrade.
Why This Matters ❓
This update enables more businesses to adopt stronger identity security without additional licensing overhead. Token Protection helps close one of the most commonly exploited gaps in the authentication flow - session hijacking.
Even with MFA in place, if a bad actor gets access to a token (e.g. through phishing), they may still gain access. Token Protection breaks that attack chain.
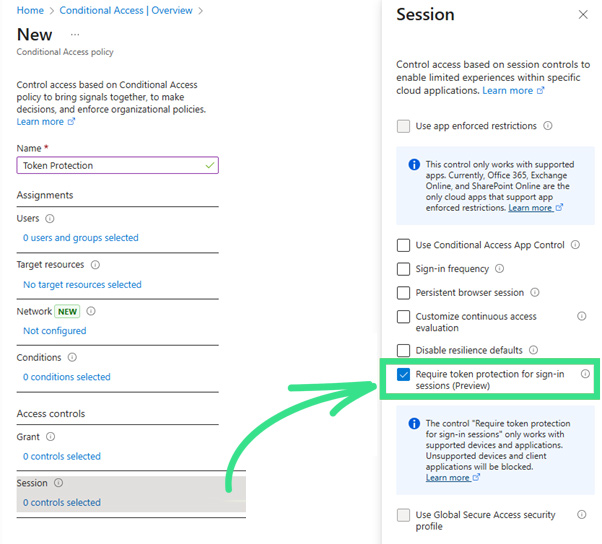
How to Set Up Token Protection ?
To configure Token Protection via Conditional Access, follow these steps:
- Log in to the Entra Admin portal with Conditional Access admin rights.
- Navigate to:
Microsoft Entra ID > Protection > Conditional Access > Policies - Create a new policy targeting:
- A pilot group of users
- Cloud apps such as Exchange Online, SharePoint Online, and Windows App (if using Azure Virtual Desktop or Windows 365)
- Conditions set to include Windows-only device platforms and exclude browser clients
- Under Access Controls > Session, enable Token Protection
- Start in report-only mode to monitor and assess before enforcing
Supported Platforms & Applications ⚒
Token Protection works for:
- Device Types: Windows 10+ (Azure AD joined, hybrid-joined, or registered)
- Apps:
- OneDrive sync (v22.217+)
- Microsoft Teams (desktop)
- Power BI (desktop)
- Exchange PowerShell
- Visual Studio 2022+
- Windows App for Azure Virtual Desktop & Windows 365
⚠️Not Supported (yet):
- Web-based apps (e.g. Teams Web, Outlook Web)
- iOS/Android mobile apps
- Devices like Surface Hub, shared devices, bulk-enrolled endpoints
Part of a Larger Zero Trust Model
Token Protection isn’t a silver bullet—but it’s a valuable addition to a layered Zero Trust security strategy. It complements:
- Phishing-resistant MFA (FIDO2, Passkeys)
- Risk-based Conditional Access
- Network-based access control (via Global Secure Access)
- Continuous sign-in monitoring
Summary
Token Protection is now live for Entra ID P1—offering a practical and powerful way to block stolen refresh tokens from being reused on other devices.
If you’re already using Conditional Access policies and enrolled Windows devices, this is a no-brainer addition. Just be sure to start with a test group and monitor closely before full rollout.
Need help enabling this or reviewing your current Conditional Access policies and/or overall IT Support Services? Contact us at Prime Networks and we’d be happy to help strengthen your identity security posture.
☎️020 7443 5618
✉️info@prime-networks.co.uk